Here are the various new capabilities and improvements available in Enhanced Audio/Video Experience. A new setting is now available to hosts to prevent recording downloads by viewers. Individual attendees will be able to turn it on/off for themselves from the microphone menu if the host has enabled beta features for the room. Change your passwordto help maintain the security of your account. Your Apple ID is the account you use to access Apple services like the App Store, Apple Music, iCloud, iMessage, FaceTime, and more.
- To enable this dimming functionality, choose either of the first two options.
- In cases where the output option is set to file, the template file will have a vanilla injection routine which is designed just to test if the decryption routine works.
- More practically, this means that some built-in Windows programs always run in a high integrity context.
- The mitigation for most of the described methods is quite simple.
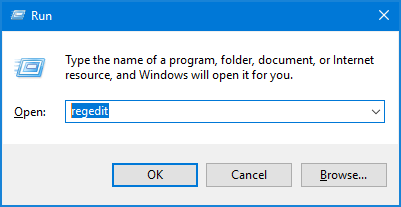
Decrpyting an encrypted .dll and other files using Termux app (5.0 and up). @DannyNiu this article is about polymorphic viruses, which are difficult to detect, for example, by file signatures because they change their file signatures. It does not say that Windows 10 kills all programs that apply cryptography to code segments/sections.
Effortless Advice Of Dll – What’s Needed
Limit the ability to run applications and scripts that can be used to enumerate or exploit privileges. Approval lists control which applications and scripts can execute. Deny lists control which known malicious applications and scripts are blocked or require additional auditing.
- ”, or something about gobbling up those that wish to cross the bridge.
- 【Advanced Software Features】Prioritize your traffic and guarantee high quality of video or voice data transmission with Port-based 802.1p/DSCP QoS and IGMP Snooping.
- Elevate without prompting Allows privileged accounts to perform an operation that requires elevation without requiring consent or credentials.
How a track you have heard a hundred times on dozens of different setups connects with your inner music fan, and whether it adds or subtracts anything from the tracks you are hearing. As this is a demo unit, it didn’t come with the retail packaging. From what I have seen online, the full retail kit will certainly look the part, but as of right now I can’t confirm what exactly that will be. In the demo pack was included the new QP2R dock and a high end USB to USB-C cable, both of which exude a nice feel of solidity and https://windll.com/dll/microsoft-corporation/wldcore high quality build.
Easy Programs Of Dll Errors Revealed
Once the UAC pops up then the background screen will be in active and you cannot do any activity other than cancelling or enter the admin password to continue. Some legacy applications would directly interact with certain parts of the file system and registry.
BloodHound is a single-page Javascript web application, built on top of Linkurious, compiled with Electron, with a Neo4j database fed by a C# data collector. It uses graph theory to reveal hidden and often unintended relationships within an Active Directory environment. Getting access to both the SYSTEM and SAM database could allow an attacker to extract the hashes. If the original password was a weak, reused password, it’s very likely the attacker can crack it. In Windows, the SID is how the operating system refers to accounts and processes, instead of using an account or process name. Unfortunately, many organizations rely on out-of-the-box roles. When unsure which role to assign to Users, most delegate Local Administrator privileges.

